This morning I was greeted by vCenter with high CPU utilization on all my VDI ESXi host. vCent alarm shows that it started at around 1AM. My gut feeling tells me that it was a scheduled network vulnerability scan or misconfigured McAfee EPO on Virus scan. Looking at various logs did not really revealed any evidence of such but I spent about 3 hours carefully looking cause I wanted to pin the blame on another group (I’m sure someone can relate).
I started looking carefully at “taskhost” in Task Manager since this is the one consuming the most CPU on multiple sampled machine. The problem is that “taskhost.exe” is the process for scheduled task and your really need to use Process Explorer to really get more info about the process. I don’t know any other tool that will do it other than Process Explorer.
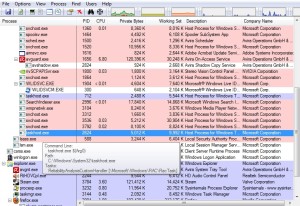
I look for taskhost.exe that has high CPU utilization. The image does not show multiple taskhost but on one of my vm there was about 2 or 3 depending on the running task at the time. I hover my mouse on the taskhost.exe to see the details. I am interested in the last line “\Microsoft\Windows\RAC\RacTask”, this is the path on the task scheduler.
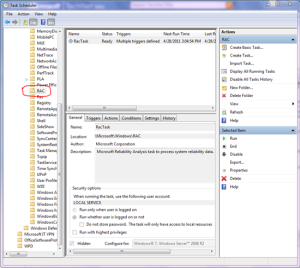
Checking the details of the task shows that it gets triggered two ways. Mine was triggered by EventID:1007. Now I did not have time to investigate the event and besides I don’t think I would need Reliability Monitor on my VDI environment taking up precious CPU resources.
THE FIX:
– Finding it was the hard part, the fix is real easy. The fix is just to kill the process via the GUI or command line. Once I issue the command I see the Task Manger CPU utilization effect immediately.
SCHTASKS.EXE /end /tn \Microsoft\Windows\RAC\RacTask
– To stop it from re-occurring I disable the task:
SCHTASKS.EXE /change /disable /tn \Microsoft\Windows\RAC\RacTask
Now to send it on all virtual machines you can use so many different tools of your choice. If you want something free you can use PSEXEC by Microsoft Sysinternals. Just read up on how to do it, there’s plenty of resources online.
http://technet.microsoft.com/en-us/sysinternals/bb897553.aspx
psexec.exe -accepteula \\remotecomputer “c:\Windows\System32\schtasks.exe /end /tn \Microsoft\Windows\RAC\RacTask”
psexec.exe -accepteula \\remotecomputer “c:\Windows\System32\schtasks.exe /change /disable /tn \Microsoft\Windows\RAC\RacTask”
DISCLAIMER: Sorry I did not really test my syntax on PSEXEC, I’m just doing it from memory. We use PDQ Deploy (There’s free one) on this particular one; GFI Languard is another tool that can do it.
Just to be sure I added “c:\Windows\System32\schtasks.exe /change /disable /tn \Microsoft\Windows\RAC\RacTask” on startup scripts for those once PDQ missed. It will be a good idea to update my gold image. I use the old Quest vWorkspace Desktop Optimizer but I guess this setting is untouched using the tool.
That is it, good luck.